As the world continues to digitize, storing data in a digital format becomes a standard across all business sectors. In today’s information age, businesses need fast access to their data to communicate with customers, vendors, and perform their daily work operations. Losing access to digital assets -as a result of ransomware attacks– can have catastrophic consequences on the victim company that range from losing access to company data permanently, possibly, a complete shutdown of business operations –which can result in millions of dollars in lost revenue- in addition to the financial and reputation damage. #ec1e28

Ransomware is a type of malicious software that prevents victims from accessing their computing device files using various methods unless a payment (ransom) is made. The victim system can also become infected with other types of malware (e.g., spyware) once a successful attack occurs. No one is immune to ransomware attacks. Recent incidents show that individuals, public and private organizations (both large corporations and small and medium-sized companies (SMEs)) fall victim to this type of attack. Unfortunately, there is no sign that the ransomware threats will slow down in the future. On the contrary, all signs point to a massive increase in ransomware attacks, especially after seeing the vast attacks against health care organizations during the current Covid-19 pandemic.
Cybersecurity Ventures has published frightening statistics about the projected damage of ransomware attacks in the coming years. For instance, it predicates that global ransomware damage is estimated to reach $20 Billion (USD) by 2021. The same report estimated that a ransomware attack would hit business every 11 seconds by the end of 2021 without counting attacks against individual users. Keepnetlabs published a report about Ransomware and SMEs; it estimated that the average ransom demand is $84,000 today and 1 in 3 companies pay the ransom today; the same report concluded that 1 in 2 organizations was attacked by ransomware in 2019 and attackers succeeded in encrypting the data in 73% of these attacks.
This article will introduce the term ransomware, talk briefly about its history, differentiate between its types, see how a ransomware attack executes practically, and list the primary attack vectors utilized by ransomware operators to infect computer systems.
RANSOMWARE ATTACKS HISTORY
The first recorded usage of ransomware took place in 1989 and was called AIDS Trojan. The attacker, a biologist named Joseph Popp, sent 20,000 infected floppy disks through mail to the World Health Organization’s AIDS conference attendees. The disks were labeled “Aids Information – Introductory Diskettes” and contained an interactive questionnaire used to trigger the ransomware after approximately 90 reboots of the victim’s computer.
The AIDS Trojan ransomware turns victims’ Windows operating system unusable by hiding all directories and locking files on their computer’s hard drive. To remove the lock, the victim had to pay $189 to a Panamanian post-office box.
RANSOMWARE ATTACK TYPES
We can differentiate between two ransomware types: crypto and locker ransomware.
- Crypto (Encryption) ransomware: This is the most prevalent type of ransomware. It works by encrypting all victim data and hold it hostage until a ransom is paid. Crypto ransomware does not intend to damage the underlying operating system because it needs it to remain operational so the victim can pay the ransom. Some crypto-ransomware variants steal personal and business files from the victim’s device and threaten to release them to the public if they refused to pay the ransom. This type of ransomware is also known as Dox-ware.
- Locker Ransomware: This is a light version of ransomware. It works by preventing a victim from accessing their files by locking the desktop or login screen and then demanding a ransom to remove the restriction.
Cybercriminals mainly utilize encryption ransomware strains to extort money from their victims. Recent ransomware attacks show the massive damage that encryption ransomware can bring to victim organizations. One of these incidents is the attack against the City of Lafayette, Colorado. They were forced to pay $45,000 to ransomware operators after their computers and data became encrypted via ransomware on July 27.
HOW DOES RANSOMWARE WORK?
Ransomware can access victim devices using different methods, such as SPAM and phishing email, exploit kits, pirated and internet programs, compromised websites, infected USB devices in addition to Malvertising, and Microsoft Office Macro. However, the most common one is through phishing emails. An adversary sends an email message containing a malicious attachment (such as a portable executable (PE) file, an MS document, or a JavaScript file) –or contains links to a website housing the malware. Once the victim downloads and opened the malicious attachment, the ransomware begins executing its malicious routine.
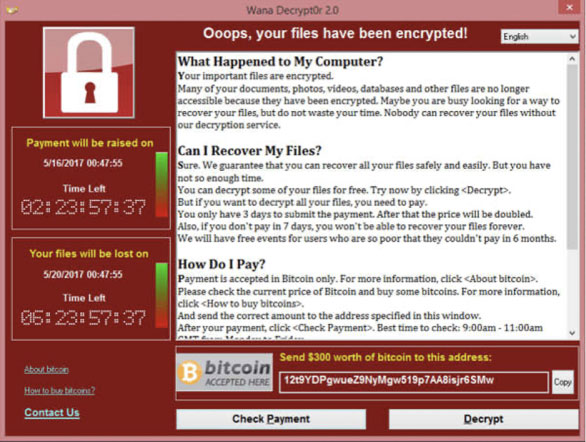
Once installed on the target device, crypto-ransomware starts searching for files (commonly targeting files with specific extensions such as MS Office files and backup files) and encrypting them. Once finished, the ransomware will announce its presence on the victim device screen by showing a ransom note (see Figure 1) containing instructions to pay the ransom to regain access to hostage files. Most ransomware families request payment through Bitcoin cryptocurrencies, because it is extremely difficult to track payment through this method.
RANSOMWARE ATTACKS VECTORS
Ransomware operators use various methods to infect victims with ransomware; the following are the main ransomware infection methods.
- Phishing email: Email service is still the primary vehicle used to infect victims with different malware types, especially ransomware. A recent report published by Verizon found that almost all malware arrived on computers via email: this was true in 94 percent of cases.
- Malvertising: Cybercriminals abuse legal online advertisement channels (e.g., Google Adsense) to infect victims with ransomware, by injecting malicious code that directs unaware internet users to a malicious website or a compromised server housing an exploit kit.
- Exploit kits: Cybercriminals direct unaware internet users to compromised websites hosting exploit kits using various methods (e.g., utilizing Malvertising). When the victim reaches the compromised site, an exploit kit will scan the victim’s computing device for vulnerabilities (e.g., unpatched operating system or outdated applications) and tries to exploit them to install the malicious software silently without user knowledge.
- USB and Removable Media: This is an old-school attack technique. However, it still very effective in distributing malware. Once a victim inserts the compromised USB device into a device, it will install the malware automatically. Some malware types—like ransomware and worms—can propagate and infect all computers connected to the same network.
- Office Macros: Malicious MS office documents –especially the one downloaded from the internet- can be exploited by cybercriminals to download and install ransomware on the victim’s device.
- Pirated software: Pirated programs and software downloaded from the internet can be abused to conceal malware within it, which will install silently when the user executes the program’s original installer.
SUMMARY
The ransomware threat is occupying the media headlines these days and will continue in the future. Ransomware operators target all organization’s types and sizes. However, many studies conclude that small businesses are the preferred target because they spend less on cybersecurity software/hardware and staff training. Many of them are underestimating the danger of ransomware attacks. They think their small size makes them unattractive to ransomware operators; however, this is entirely wrong.
CITATION
Khera, V., 2021. Introduction to Ransomware Attacks. [online] Linkedin.com. Available at: https://www.linkedin.com/pulse/introduction-ransomware-attacks-dr-varin-khera-1c/ [Accessed 30 June 2021].
Contact Cloudsec Asia today to safeguard your organization against cyber threats.
We are your premier cybersecurity solution and consulting provider in the APAC region
