Social Engineering (SE), In the information security context, is a kind of cyber-attack that uses psychological tricks in person, over the phone, or via the internet (e.g. email messages, social media messages) to convince unaware users to reveal sensitive information about themselves(e.g., online accounts credentials, personal information, and financial information)
or about the organization they work for (e.g., IT infrastructure, implementing security solutions such as antivirus and firewalls, types of access controls, key employees holding access to sensitive resources).

Some Social Engineering attacks aim to deceive a victim into installing malicious programs on his device to gain full control over it and to use it to spread the infection to other places within the network. Cybercriminals found it is easier to exploit human errors to gain entry into the targeted network instead of launching direct attacks against it.
For instance, granting access to critical resources within a network by fooling unaware user to give his/her account credentials is more straightforward than launching brute-force attacks or trying to exploit software/hardware vulnerabilities to gain the same info. This makes SE attacks pose a real threat to any organization because no one can predicate human behaviors when facing a social engineering attack making this type of attack very serious when executed successfully.
Social Engineering attacks can be grouped into two types according to the method used to execute the attack:
- The first one -is the most popular- and it depends on the internet –especially email phishing.
- The second type depends on the phone and in-person tricks to deceive the victim.
Nevertheless, many attacks utilize both types to convince the victim to reveal confidential information. Let us start talking about the most popular SE attack type, which is phishing emails.
E-MAIL PHISHING ATTACKS
“Email service is still the primary vehicle used by cybercrimes to launch different types of cyber-attacks.”
A phishing email is a kind of Social Engineering attack that uses the regular email service, social media services messaging functions (e.g., Facebook, Twitter, Instagram), or even internet messaging applications such as WhatsApp; the message appears to be originating from a reputable source with the goal to acquire confidential information from the target or to trick him/her into installing a malicious program (e.g., ransomware, Trojan) delivered via email attachments or malicious links on victim’s device.
To understand how a phishing email deceive internet users, it is beneficial to know the general format of a phishing email (see Figure 1).
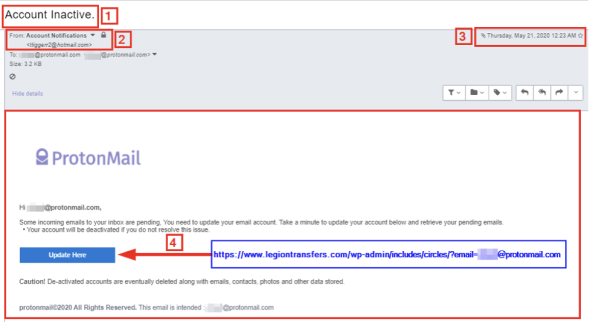
From Figure 1, we note the following:
- Email subject line: Attackers tend to use threatening language; they use scarring and urgent words to push the recipient to act quickly under speed stress without thinking. According to Barracuda Networks’ “Spear Phishing: Top Threats and Trends” report, the most used phishing emails subjects: Request, Follow up, Urgent/Important, Urgent Attention, Are you available? /Are you at your desk? Payment Status, Invoice Payment Required, Hello, Purchase, Invoice Due, Re:, Direct Deposit, Expenses, and Payroll.
- Sender Email: The sender uses an email address hosted on hotmail.com. However, the email is pretended to be from the ProtonMail email provider. This is a clear clue that this email is not originated from the pretended sender. There are many services to investigate the sender domain name to see if it is listed as malicious.
The following are some free services to analyze suspicious URLs: Norton Safe Web (https://safeweb.norton.com) IsItPhishing (https://isitphishing.org)Phishtank (https://www.phishtank.com)Virus Total (https://www.virustotal.com/#/home/url)Kaspersky VirusDesk (https://virusdesk.kaspersky.com
- Email date/time sent: Check the date/time when the email was sent. If the email pretends to be from your organization or bank, did they send it during official work hours? Check the date also. Did they send it during holidays or a general shutdown?
- Investigate email content: Hover your mouse over all hyperlinks that existed within the email body to reveal the actual URL; in my example, the “Update Here” button should point to ProtonMail.com; however, it redirects to another domain name https://www.legiontransfers.com/wp-admin/includes/circles.
A practical scenario of how Social Engineering attacks work against individuals and organizations:
- An individual’s sensitive information can be acquired through impersonating a trusted entity such as his bank, a government entity, Internet Service Provider (ISP), or a social media service -that the target has an account with- to lure him into revealing sensitive information (by asking him to fill an online form or by sending the confidential information via the email). Once the attacker obtains target info, he can use it to blackmail the victim by accessing his/her personal data stored in cloud services or personal email accounts.
The attacker can also make unauthorized purchases using the victim’s stolen credit card info or use stolen information (e.g., employee login credentials) to gain unauthorized access to the victim organization’s protected resources.
In addition to stealing victim sensitive info, adversaries can utilize phishing emails to install a keylogger on the victim device to silently steal and monitor his online activities.
- In an enterprise environment, SE attacks can have catastrophic consequences. For instance, most Advanced Persistent Threat (APT) criminals groups use phishing emails as the primary means to surpass all network security perimeters (Firewalls and IDS) to infect and propagate malware in enterprise network environments. They achieve this by infecting victim endpoint device and then spread to all connected devices within the network.
Although the internet is still the preferred medium for attackers to launch Social Engineering attacks, however, other methods -which do not depends on the internet- are still used by criminals to acquire sensitive information that can be used to attack IT systems. The following are examples of other common Social Engineering attacks.
- Shoulder surfing: In this type, the adversary steals confidential information from users while performing their regular tasks. For example, an attacker can capture a user’s password by watching them type it on the keyboard.
- Dumpster diving: In this type, an adversary tries to collect sensitive information from materials thrown in the trash. For instance, many organizations dispose different types of paper documents without shredding them first (e.g., calendar of meetings, users list, and system usage manuals). This insecure practice is not limited to papers, as many organizations dispose old computing devices without securely wiping data on the devices’ hard drive. Adversaries can retrieve sensitive information by looking in the garbage or by recovering data from old computers’ hard drives using various data recovery software.
- Role-playing: In this attack, an intruder will impersonate a legitimate person (e.g. technical support or customer service staff) and try to take sensitive information from users to gain unauthorized access to their online accounts.
- Keyloggers/Trojan horses: This attack works by infecting the victim’s device with stealing malware (e.g., monitoring software). For example, an adversary tricks the user into installing malware on his device (e.g., by opening an email attachment containing the malware or downloading free internet programs such as games or screen savers bundled with malware within it).The malicious program will record everything the user types on the keyboard and see on a computer screen and send it back to the attacker. An attacker can acquire various sensitive information to impersonate the victim or gain unauthorized access to his/her online accounts.
- Open source intelligence (OSINT): OSINT is an intelligence-gathering rather than an attack method. Cybercriminals use it extensively to collect intelligence from publicly available sources about any target (individual or organization) in today’s information age. The collected information is used to customize an attack for a specific target (e.g. crafting a spear-phishing email to target a CEO). An example of data gathered using OSINT sources is utilizing the WAY BACK machine service to retrieve old versions of a web page. Previous versions may contain important information (e.g., contact information such as phone numbers and email addresses, files metadata) in the past (see Figure 2).

SUMMARY
There are different types of social engineering (SE) attacks. All try to compromise target confidetial information by exploiting the “human psychology” which remains the weakest element in any information security defense strategy. Educating users about the different types of SE attacks and how each one executes is still the primary defense to counter these types of attacks.
Citation: Khera, V., 2021. A Practical Introduction to Social Engineering Attacks. [online] Linkedin.com. Available at: https://www.linkedin.com/pulse/practical-introduction-social-engineering-attacks-dr-varin-khera/?trackingId=cDHWvFUlQNOMhqNZPy1OMQ%3D%3D [Accessed 30 June 2021].
Connect with us today at www.cloudsecasia.com to safeguard your organization against cyber threats.
We are your premier cybersecurity solution and consulting provider in the APAC region
